Progress
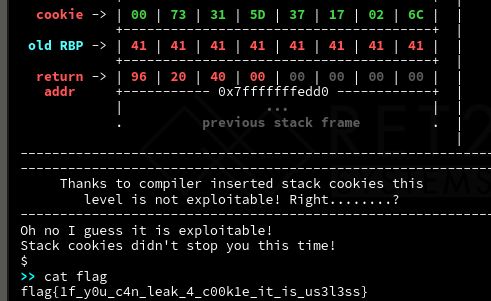
Latest: solved Mission 1, currently on the Stack Cookies lesson (third lesson). Captured another flag today.
About the course
RET2 Systems' Fundamentals of Software Exploitation trains students to read and reason about C/C++ programs, reverse engineer 64-bit Linux binaries, and craft python exploits to demonstrate and bypass modern mitigations.
- Focus: x86-64 assembly, ELF analysis, exploit development
- Mitigations covered: Stack Cookies, DEP (NX), ASLR, PIE
- Techniques taught: Shellcoding, ROP, stack pivoting, information leaks
- Bug classes: Heap overflows, use-after-free, integer issues, race conditions
- Outcome: ability to do independent vulnerability research against closed-source apps
Why I'm doing this
RET2 is excellent training for anyone doing low-level offensive work. I'm honing exploit skills by reading assembly, debugging ELF binaries, and turning memory-corruption bugs into reliable PoCs. Every lab sharpens my C internals knowledge and makes real exploit development feel doable.
Notes / links
Course: RET2 Systems — Fundamentals of Software Exploitation WarGames
Suggested prerequisites: familiarity with C & Python, ELF, GDB, and basic assembly. I'll post flags / writeups here as feasible.